HACKING:
Mayhem — A New Malware Targets Linux and FreeBSD Web Servers
Security researchers from Russian Internet giant Yandex have discovered a new piece of malware that is being used to target Linux and FreeBSD web servers in order to make them a part of the wide botnet, even without the need of any root privileges.
Researchers dubbed the malware as Mayhem, a nasty malware modular
that includes a number of payloads to cause malicious things and
targets to infect only those machines which are not updated with
security patches or less likely to run security software.
So far, researchers have found over 1,400 Linux and FreeBSD servers around the world that have compromised by the malware, with potentially thousands more to come. Most of the compromised machines are located in the USA, Russia, Germany and Canada.
Three security experts, Andrej Kovalev, Konstantin Ostrashkevich and Evgeny Sidorov, who work at Russia-based Internet portal Yandex, discovered the malware targeting *nix servers. They were able to trace transmissions from the infected computers to the two command and control (C&C) servers.
"In the *nix world, autoupdate technologies aren't widely used, especially in comparison with desktops and smartphones. The vast majority of web masters and system administrators have to update their software manually and test that their infrastructure works correctly," the trio wrote in a technical report for Virus Bulletin.
"For ordinary websites, serious maintenance is quite expensive and often webmasters don't have an opportunity to do it. This means it is easy for hackers to find vulnerable web servers and to use such servers in their botnets."
Researchers say that this new type of malware can work under restricted
privileges on the systems and has been created by keeping multiple
functionality in mind. The malicious attack is conducted via a more
sophisticated PHP script, that has a low detection rate with the
antivirus engines available.
Communication of the system is established with the command and control
servers, which can send the malware different instructions. As we
mentioned above that Mayhem is a modular, its functions can be expanded
through plugins and at the moment some eight plugins have been
discovered, those are listed below:
- rfiscan.so - Find websites that contain a remote file inclusion (RFI) vulnerability
- wpenum.so - Enumerate users of WordPress sites
- cmsurls.so - Identify user login pages in sites based on the WordPress CMS
- bruteforce.so - Brute force passwords for sites based on the WordPress and Joomla CMSs
- bruteforceng.so - Brute force passwords for almost any login page
- ftpbrute.so - Brute force FTP accounts
- crawlerng.so - Crawl web pages (by URL) and extract useful information
- crawlerip.so - Crawl web pages (by IP) and extract useful information
In case of rfiscan.so, the malware spreads by finding servers
hosting websites with a remote file inclusion (RFI) vulnerability that
it checks using ‘http://www.google.com/humans.txt’ file. If the HTTP response contains the words ‘we can shake’, then the plugin decides that the website has a remote file inclusion vulnerability.
Once the malware exploits an RFI, or any other weakness mentioned above,
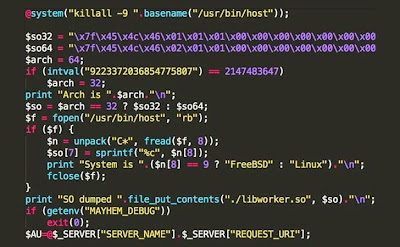
and get installed, it will run a PHP script on a victim. The PHP script
kills all ‘/usr/bin/host’ processes, check for the system
architecture and OS (whether Linux or FreeBSD), and then drops a
malicious object identified as ‘libworker.so’.
Meanwhile, the PHP script also defines a variable named ‘AU’,
which includes the full URL of the script being executed. It also
executes the shell script which is then being executed, then pings its
Command-and-Control server.
The malware then creates a hidden file system, known as sd0, and downloads all the above eight plugins, none of which were detected by the VirusTotal malware scanning tool.
Mayhem was first detected in April 2014, and according to the trio, it is a continuation of the “Fort Disco” brute-force campaign that was unearthed by Arbor Networks in 2013.
The Yandex researchers warned people that there may be more plugins in
circulation, based on information they discovered on the two detected
Command-and-Control servers, including one which specifically exploits
the systems that haven’t patched the critical Heartbleed vulnerability in OpenSSL.
Did this Post help you? Share your experience below.
Use the share button to let your friends know about this update.
DONATE! GO TO LINK: http://kosullaindialtd.blogspot.in/p/donate.html
Did this Post help you? Share your experience below.
Use the share button to let your friends know about this update.
WANT TO DONATE FOR SITE?
DONATE! GO TO LINK: http://kosullaindialtd.blogspot.in/p/donate.html



Looking for Norton Support visit our website or reffer our blog for Norton Antivirus trouble shooting "norton security tech norton internet security login sonar protection not fixed windows 10
ReplyDelete"
This is a very useful blog that you shared with us,
ReplyDeletethank you
regards
hiring hacker
Thanks for the information.
ReplyDeletealso, join Linux course in Pune